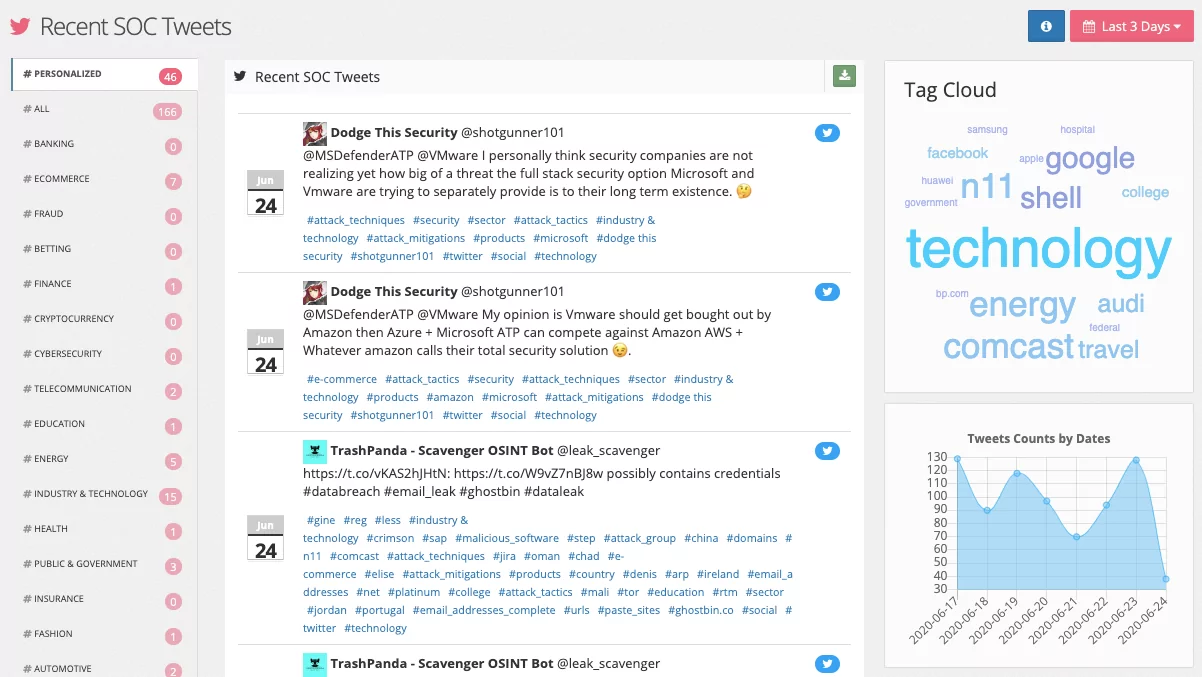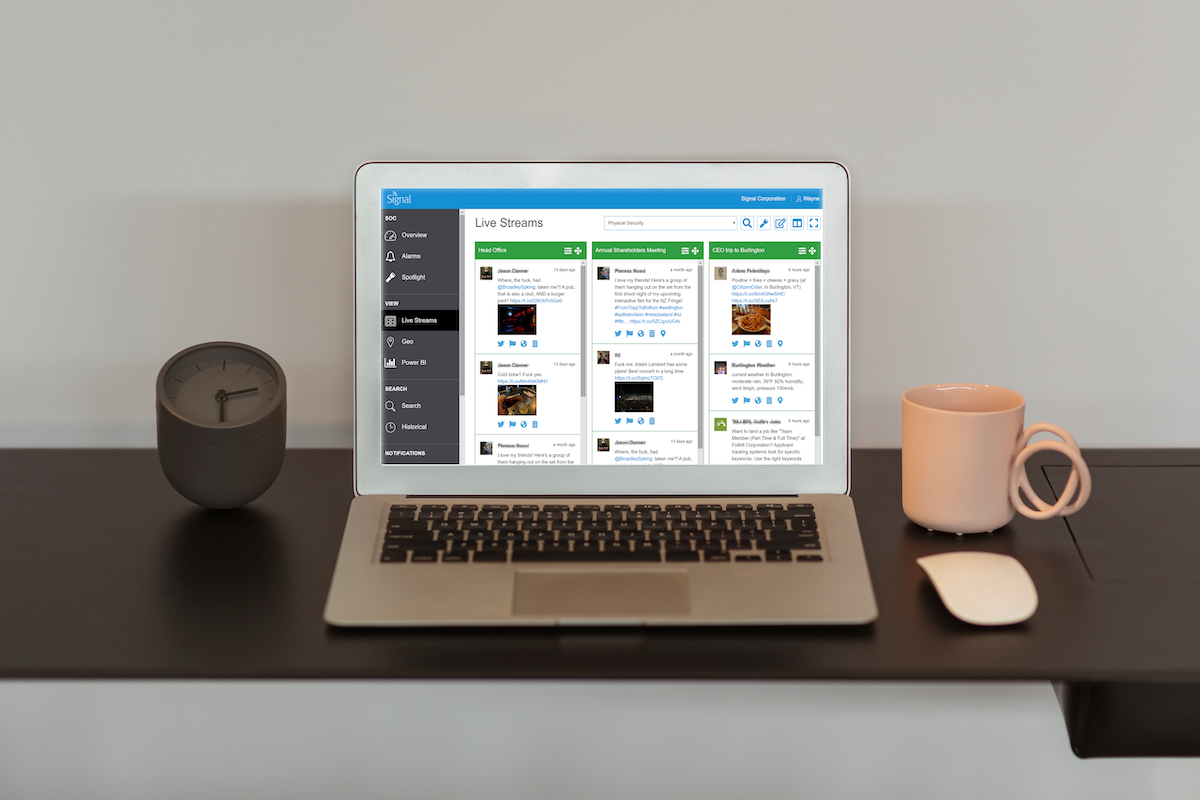
Why Government Use of Social Media Monitoring Software Is a Direct Threat to Our Liberty and Privacy | News & Commentary | American Civil Liberties Union
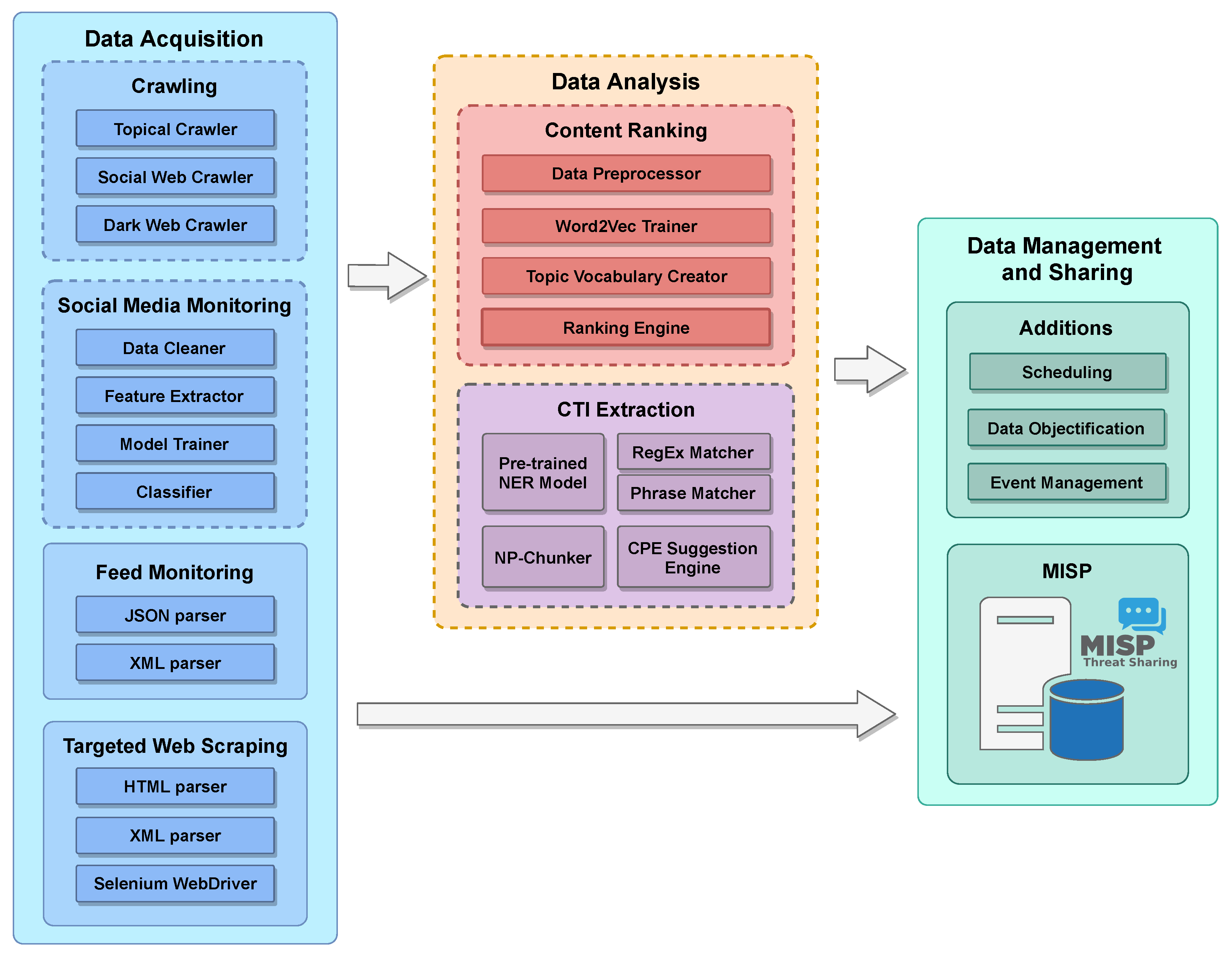
Electronics | Free Full-Text | inTIME: A Machine Learning-Based Framework for Gathering and Leveraging Web Data to Cyber-Threat Intelligence

![PDF] Insider Threat: Enhancing BPM through Social Media | Semantic Scholar PDF] Insider Threat: Enhancing BPM through Social Media | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ea050eaf6302e5892ef0558506164ae5f63434c1/3-Figure1-1.png)